What Department Combats Counterfieting by Designeing New Ways
Suggested Citation:"5 Counterfeit-Deterrent Strategies." National Research Council. 1993. Counterfeit Deterrent Features for the Next-Generation Currency Design. Washington, DC: The National Academies Press. doi: 10.17226/2267.
×
5
COUNTERFEIT-DETERRENT STRATEGIES
A comprehensive counterfeit-deterrence program for U.S. banknotes must contain many elements to respond to the threats discussed throughout this report. This chapter summarizes those elements that can be used to formulate a comprehensive national strategy that can reduce future counterfeiting incidents of U.S. banknotes. Such a strategy entails far more than a one-time incorporation of a new set of counterfeit-deterrent features in banknotes. Required is a guiding philosophy that includes responding to emerging threats before they become a significant problem; identification, selection, and rapid incorporation of appropriate deterrent features; use of devices to aid authentication of banknotes (i.e., using more than visual inspection alone); public education and acceptance of the changes; implementation of appropriate law enforcement strategies; and continuing exchange of information with other countries of the world.
It is commonly accepted that at least half of the solution to a problem consists of the recognition of it, plus careful and complete definition of it. Thus, the increasing awareness by the U.S. government regarding the counterfeiting threat and its growing severity is the critical step toward the derivation of an effective, anticipatory, multifaceted, anticounterfeiting program.
The recently established anticounterfeiting task force composed of representatives from various agencies within the Department of Treasury (including the BEP, the Federal Reserve, and the Secret Service) is a very positive step. This task force will be far more credible and effective than any of the individual members acting alone.
RESEARCH AND DEVELOPMENT STRATEGIES
Technology Advancements
A long-term deterrent strategy must anticipate and lead the evolution of reprographic systems and the level of expertise of the counterfeiting community. Technological progress in nonimpacting printing will continue to be driven by many market forces in a never-ending quest for accuracy and quality, and it is imperative that the Department of Treasury be kept informed of developments in ample time to respond to a future threat. In the same manner, the skill level of counterfeiters will change as they attempt to improve their craft. Continuing information must be provided in these two areas.
Suggested Citation:"5 Counterfeit-Deterrent Strategies." National Research Council. 1993. Counterfeit Deterrent Features for the Next-Generation Currency Design. Washington, DC: The National Academies Press. doi: 10.17226/2267.
×
Appropriate mechanisms for the Department of Treasury to stay up-to-date can include the use of advisory panels, committees, workshops, and briefings that address technological advances in reprographics and a continuing forensic evaluation of counterfeiting techniques and methods. In the latter case, knowing that a counterfeit has been created and its production eventually stopped is a reaction mode of operation and is the domain of the Secret Service; the Treasury Department along with the Federal Reserve Board should anticipate advances in the level of sophistication of the counterfeiter, adjust the type and timing of deterrent features accordingly, and perform in a proactive mode.
There is a considerable amount of scientific and technological work underway in university, industrial, and government research laboratories that could have relevance for future counterfeit deterrence. However, the link between these research results and the BEP's needs would not normally be made in a timely way unless the efforts were specifically geared to that end.
Cases in point are the many emerging photonic materials that can serve in the future as active deterrent features that is, they can make the counterfeit bill look outstandingly different. One class of candidates would be photo-induced charge-transfer complexes. These materials, of which there are a large number, change their light-absorption characteristics upon exposure to intense light. The mechanism involves the transfer of an electron from a "donor" molecule to an "acceptor" molecule when activated by photonic energy. For example, a copy of an image printed in an ink that contained such material would show a "color" (usually dark green, brown, or black) where there was none apparent in ambient light for the genuine banknote. Many of these reactions are completely reversible.
Another class of photonic materials that may some day be useful are those that exhibit nonlinear optical properties, such as some fullerene derivatives. They convert long wavelength light to shorter, more energetic wavelengths. These materials can be used to shift light wavelengths in interesting, and perhaps useful, ways, such as for light-frequency doubling with photo-emitting compounds. Nonlinear optical materials combined with reversible saturable absorbers (i.e., in which light transmission decreases as exposure increases) may also lead to very useful combinations of future features. These materials are not now suitable for use in banknotes, but further dramatic developments can radically change this assessment. There are many other such examples.
In the recent past, the counterfeiting-deterrence research and development program at the BEP has drawn primarily on external technical work, with little internal research. This balance may be shifting; the BEP recently announced the formation of the Security Technology Institute within the organization (Church, 1993). The breadth and quality of the investigations, procurements, and external research and development support of anticounterfeiting methods, techniques, and materials has improved considerably since the earlier National Materials Advisory Board studies. The committee strongly supports a more balanced approach between external and internal work, as long as the internal work does not duplicate external efforts. Internal research and development activities that included a
Suggested Citation:"5 Counterfeit-Deterrent Strategies." National Research Council. 1993. Counterfeit Deterrent Features for the Next-Generation Currency Design. Washington, DC: The National Academies Press. doi: 10.17226/2267.
×
component of fundamental research would permit the BEP to become a "full-fledged" member of the technical community and be able to capitalize on pertinent scientific and technological advances.
The same mechanisms suggested above for keeping the Department of Treasury up-to-date with advancements in reprographic technology and counterfeiting methods (e.g., advisory panels, committees, workshops, and briefings) would be appropriate1.However, more in-depth preparatory work would be required, since the amount and detail of information is immense. The benefit of such planned interactions would be a leveraging of the research already going on and increased awareness in the general research community regarding the needs for counterfeit-deterrent features.
Realistic Testing and Specifications
A program must be in place to continually devise and evaluate new deterrent features. An essential part of such a program would be the re-evaluation of the testing specifications and their relevance to real-world wear and tear in order to not preclude the use of some exceptionally effective features that may fail an overly demanding test. The current BEP efforts to examine the suitability of chemical resistance tests should be extended to other test specifications. Some consideration should also be given to learning how banknotes of different denominations are handled and determining if the durability requirements can be different for higher denomination banknotes.
Implementation of Changes
The BEP estimates that under normal circumstances when competitive contracting must be used, approximately 2 to 5 years are required from the time it decides to use a new deterrent feature until that deterrent appears in new currency (Sellers, 1993). (The time required for implementation can be considerably shorter if the changes can be implemented internally without the need for competitive contracting.) Approximately 1 to 2 years are required to develop the specifications, complete all the testing, and produce proofs. Up to 2 years may be required for the competitive contracting process, and 1 year for production incorporation. Additional time may be required if no offer fully meets the specification, if the proposed prices are too far above the estimated cost, etc. However, if the new feature is an upgrade to a current feature, then the process time can be shortened to about 1 year.
Thus, under normal circumstances a feature must be targeted at a counterfeiting threat well before the threat is fully realized. Counterfeiters will thus enjoy a period of time to learn
| 1 | One of the strongest recommendations of prior National Materials Advisory Board studies was the selection and use of a technical advisory group consisting of experts to serve as a "sounding board" and provide counsel, guidance, and direction to the development of advanced features. |
Suggested Citation:"5 Counterfeit-Deterrent Strategies." National Research Council. 1993. Counterfeit Deterrent Features for the Next-Generation Currency Design. Washington, DC: The National Academies Press. doi: 10.17226/2267.
×
how to simulate a feature. The security thread provides a case in point. The thread was targeted at counterfeiters who were using nonimpact printing reprographic technology. The existing supplier of currency paper originally expected to have the new paper available for the printing of the first notes with the new thread within 2 years of go-ahead. However, the introduction of the thread was delayed for a year since the supplier had difficulty in meeting all the specifications during production scale-up. Today, approximately 2 years after its introduction in Series 1990 $100 bills, only a few counterfeit notes with the security thread have been attempted. (Of course, the older notes without the thread are still legal tender.) Although these simulations would not withstand close examination, they have been successfully passed (Brown, 1993a)2. As banknotes containing the security thread become more prevalent, it is highly probable that professional counterfeiters will devote more effort to producing better simulations3.
Methods must be developed to shorten the time required to produce redesigned banknotes once the decision to proceed has been made. As color printers and copiers become more prevalent and sophisticated, effectiveness lifetimes of deterrent features may decrease, making faster response critically important. Strategies could include conducting additional production risk assessment before the changes are finalized, expediting the contracting process, and establishing a timetable for periodic assessment and replacement of, addition to, or modification of counterfeit-deterrent features.
As part of a major currency redesign effort, some visible features could be incorporated in anticipation of future threats but not initially disclosed. These features could be "held in reserve" and disclosed as the currency comes under attack. This strategy may prevent counterfeiters from having advance notice of their presence and ample time to practice their simulation. Features could also be introduced that lend themselves to further improvements and upgrading as required, without the necessity for major design changes. Of course, too many changes within too short a time period would only serve to confuse the public, making the counterfeiters' job easier.
SELECTION OF COMBINATIONS OF FEATURES
There is no single visible deterrent feature that is readily recognizable, highly durable, impractical to counterfeit or simulate, available at low cost, and easy to produce. Indeed, if a single dominating feature were employed, the currency would tend to be less secure, since that feature would present a single target for the counterfeiter. Multiple features add complexity to the counterfeiter's task and increase the number of counterfeiting steps to the point that the casual counterfeiter would "give up". A determined professional counterfeiter still may be
| 2 | A skilled counterfeiter using a lithographic printing over a pasted simulated "thread" successfully passed the new note 18 months after its introduction. |
| 3 | The BEP estimates that about half the $20, $50, and $100 banknotes in circulation now (mid-1993) contain the security thread. |
Suggested Citation:"5 Counterfeit-Deterrent Strategies." National Research Council. 1993. Counterfeit Deterrent Features for the Next-Generation Currency Design. Washington, DC: The National Academies Press. doi: 10.17226/2267.
×
tempted, but the task should be sufficiently difficult that the risk of getting caught would be high. Therefore, a combination of features will be required to provide a high level of practical counterfeit deterrence.
In general, any single deterrent feature can be simulated or overcome if the counterfeiter is creative and willing to perform the necessary additional steps. For that matter, given sufficient time and effort, any combination of features can be simulated. These tasks would not necessarily require sophisticated technical expertise or particularly expensive equipment, since simulation need not be highly accurate. The general public appears to be reluctant to observe and confront, and hence the chances are good that a banknote will only undergo a cursory inspection at the first encounter. Once a counterfeit enters the monetary system, its point of origin generally becomes "fuzzy. " Counterfeits produced with reprographic equipment are especially difficult to trace.
The most straightforward way to curb counterfeiting is at the source. A copier or computer printer can be prevented from copying a banknote by employing appropriate pattern recognition technology. The "print engine" can be taught to recognize a banknote and then refuse to operate properly until the offending print request is terminated or the equipment is reset. Such a capability would significantly discourage the casual, nontechnical counterfeiter. The effectiveness of such devices would be enhanced if a standard banknote feature, or small set of such features, was adopted by many countries; however such features must be unique to currency to preclude inadvertent disabling of the copier or printer.
Whereas the simulation of multiple deterrent features may not require expertise and sophisticated equipment, it does require an investment of time—a considerable investment if the simulations are done by hand, one at a time. The goal of a balanced system of deterrents, therefore, must be to make the process of overall simulation so time consuming that the counterfeiter is discouraged and abandons the task. This is accomplished by deploying a complementary set of features, each requiring a different simulation process. Each additional feature should address a potentially weak attribute of the existing set that is, it should add value to the overall system of deterrents. Such a defense in depth would address different reprographic technologies, different levels of counterfeiter expertise and tenacity, and the requirements of different viewing conditions for authentication. Care must be taken, however, that the overall visual effect remains balanced so that one deterrent does not dominate, lest the lesser deterrent not be carefully viewed. The combination of features must not produce an unpleasant appearance. (Examples of possible combinations are presented later in this chapter.)
The primary threat is the casual counterfeiter, defined in Chapter 2 as an individual who will attempt to use the output of a reprographics system directly without engaging in additional complicated steps needed to simulate deterrent features. Individual features that do not reproduce, or features that result in the copy appearing blatantly obvious, are therefore effective against this type of threat since an attempt will probably not be made to pass it. Any number of features that can not be easily copied or scanned satisfy this requirement; (e.g., color-shifting inks, holograms, watermarks, etc). Discouraging the hacker is more difficult and is best accomplished by having a larger number of deterrents, each requiring a different means and material for simulation. The goal here is one of attrition; overwhelm with so many tasks
Suggested Citation:"5 Counterfeit-Deterrent Strategies." National Research Council. 1993. Counterfeit Deterrent Features for the Next-Generation Currency Design. Washington, DC: The National Academies Press. doi: 10.17226/2267.
×
that the counterfeiter eventually "gives up." With the semiprofessional, deterrents should be selected that are more difficult and expensive to simulate accurately. These individuals deal in much higher volumes than the casual counterfeiter and hacker, and their product must be of higher quality. They are more subject to the economics, time and cost, of the process. Very little can be done to stop the dedicated professional except the periodic addition of new features designed to introduce delays into the counterfeiter 's "product" cycle.
As part of a system of features, the banknote substrate offers an important dimension for embedding features that are particularly useful and compatible with many other surface features. Security threads, watermarks, patterns, images, etc., may be incorporated with minimum disruption of the overall architecture. Visible only in transmission and not in reflection, they are immune to reproduction by copying or scanning means. Required is the allocation of a clear, unprinted area for viewing clarity.
In summary, the following general criteria can be considered for evaluating combinations of anticounterfeiting deterrents:
-
all those that applied to individual deterrents (see Chapter 3);
-
extent to which all three types of counterfeiters are expected to be deterred deterrence against specific counterfeiting methods e.g., color copiers/scanners /printers, photography, offset printing, etc., and deterrence against counterfeiting skill levels;
-
synergistic relationships among the deterrents;
-
range of sensors available for detecting the features, for either the manual or automated mode; and
-
how easy it would be to add, replace, or upgrade one or more of the deterrent features.
Examples of possible feature combinations are
-
color combined with variable-sized dot pattern or induced moiré;
-
print with photoluminescent ink on security thread;
-
laminated paper with watermarks on both halves to create a complex image; could also add various other transparent or low-optical-density deterrents in the same window;
-
transparent (non-metallized) hologram, kinegram, pixelgram, or zero-order submicron diffraction grating in the same window as a watermark, induced moire line pattern, or variable-sized dot pattern.
Combinations of features that score high using the above criteria should be incorporated into test banknotes. These could then be subjected to adversarial analysis to determine their deterrent effectiveness and used to gauge public acceptability through mechanisms such as focus groups.
REACTIVE AND PROACTIVE STRATEGIES
Overt, visible deterrent features in a banknote that are very difficult to reproduce serve as the most obvious means of authentication. But every feature should be viewed as having a finite lifetime, since the threat will continue to evolve as reprographic technology continues to advance and the social environment changes. The rate of counterfeiting has been observed
Suggested Citation:"5 Counterfeit-Deterrent Strategies." National Research Council. 1993. Counterfeit Deterrent Features for the Next-Generation Currency Design. Washington, DC: The National Academies Press. doi: 10.17226/2267.
×
to increase over time until changes are made. Counterfeiting using copiers and printers has been observed to be increasing at a geometric rate during the last 3 years. Therefore, additional features, or additional enforcement actions, will be needed to reverse the rate and cause it to fall back to a lower level. Not all features of interest will be ready for incorporation at the same time and hence should be planned to be phased-in over time, as needed.
Some deterrents may turn out to have a short lifespan. They may be introduced to combat a particular threat and become less effective against assault by newer equipment as reprographic systems improve. Microprint, for example, which was adequate to thwart low-resolution systems for a while, will become less effective as 400-dpi and 600-dpi systems come into wider usage. This example also indicates the benefit of not relying on a single deterrent feature.
Two general strategies that can lead to appropriate changes in currency design have been postulated. A reactive strategy is one in which no action is taken or new feature added until the counterfeiting rate reaches a relatively high level. This rate, the threshold of tolerance, is the point at which a change is made. However, a dramatic decrease in the extent of counterfeiting would also require the rapid withdrawal of the old, compromised currency from circulation. Case A in Figure 5-1 schematically depicts the reactive scenario. The counterfeiting rate increases to a high level at which time drastic action is taken, and the rate precipitously declines. It then begins to climb again as the counterfeiters respond to the new deterrent. In reality, the scenario would be much more complex than schematically indicated, so the figure is only notional. For instance, replacement of older-design currency would take considerable time. The counterfeiting rate would thus continue to climb for a while at a smaller rate, and it would not decline so sharply once the rate began to decrease.
Practical advantages of this strategy include the rapid coalescence of a consensus for change, and the high likelihood that sufficient resources will quickly be brought to bear to solve the problem. But the disadvantages are substantial. They include lost public confidence in the federal government and the prospect that the dramatic changes will be expensive and upsetting to a large portion of the public.
Aproactive strategy to currency design is one in which new features are incorporated in anticipation of future threats, before a large increase in counterfeiting occurs. Relative to the reactive strategy, this approach employs a much lower threshold of tolerance.
It is schematically depicted as Case B in Figure 5-2. The potential increase in counterfeiting rate is the same as for Case A except that action is taken to reduce the rate much sooner. Therefore, the actual rate never gets very high, relatively speaking. As before, the curves are idealized simplifications; the actual situation would be more complicated.
The practical advantages of the proactive approach include the containment of small counterfeiting problems and the orderly transition to new currency designs. A principal disadvantage is the expected difficulty of achieving a consensus for a change, since the exact magnitude of the future threat cannot be precisely known. If the threat is perceived as being low, adequate resources for counterfeit deterrence might not be made available. Also, more changes to currency design would probably be made under this strategy.
Suggested Citation:"5 Counterfeit-Deterrent Strategies." National Research Council. 1993. Counterfeit Deterrent Features for the Next-Generation Currency Design. Washington, DC: The National Academies Press. doi: 10.17226/2267.
×
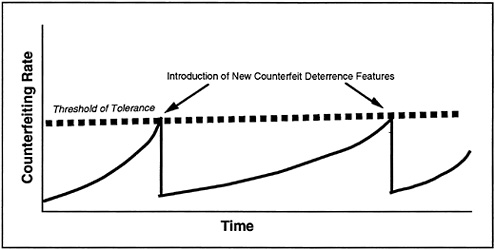
FIGURE 5-1 Case A: reactive strategy.
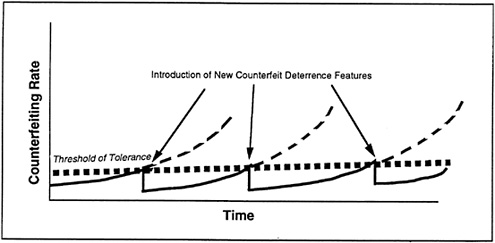
FIGURE 5-2 Case B: proactive strategy.
Suggested Citation:"5 Counterfeit-Deterrent Strategies." National Research Council. 1993. Counterfeit Deterrent Features for the Next-Generation Currency Design. Washington, DC: The National Academies Press. doi: 10.17226/2267.
×
In both cases, the threshold of tolerance curve would be shifted upward depending on the policy employed regarding the rate of withdrawal of the older currency from circulation. Figure 5-3 depicts the average age of U.S. banknotes, based on recent Federal Reserve System data. The lower-denomination bills have a relatively short lifetime compared the higher denominations, but the higher denominations are those that present the most attractive counterfeiting targets. Therefore, phase-in of changes should start with large denomination bills.
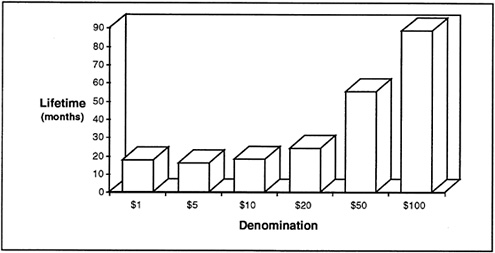
FIGURE 5-3 Average lifetimes of U.S. banknotes.
In line with this approach, phasing-in deterrents over time requires the adoption of a long-range plan that anticipates the deployment of a new deterrent with minimum overall design impact. Establishment of a base design should take into account the requirements of future additions so that the visual appearance of a banknote would not markedly change. An example would be a design that contains clear (unprinted) areas on both sides of a note for the eventual incorporation of a localized watermark. The general goal is to maintain design integrity and avoid a patchwork visual appearance.
An old visible deterrent, made obsolete by the latest technology, may still serve a purpose as it will continue to be useful against lower-level reprographic technologies. Also, its absence may be noted by a substantial portion of the public and be cause for false rejections. Discontinuance of a deterrent also presents the counterfeiter with a somewhat easier task, as it may eliminate extra steps required for simulating the feature. Upgrades or changes to a deterrent to render it more effective should be considered as a relatively fast and inexpensive option for improving security. One example, mentioned in the previous chapter, is the possibility of changing the location or width of the security thread, or the number of security threads, according to banknote denomination.
Suggested Citation:"5 Counterfeit-Deterrent Strategies." National Research Council. 1993. Counterfeit Deterrent Features for the Next-Generation Currency Design. Washington, DC: The National Academies Press. doi: 10.17226/2267.
×
However, there may be a cost penalty associated with retaining a less-effective feature, and this must be weighed against the value of retention. Also, there is only so much "real estate" on the banknote; at some time, features will have to be removed to make room for newer ones.
VALIDATION/DETECTION DEVICES
In order to accelerate and standardize the authentication process, the use of low-cost, relatively unobtrusive devices should be considered, particularly at point-of-sale locations. Just as reading the magnetic stripe on a credit card is universally accepted as normal, devices that enhance the visibility of deterrent features may facilitate the detection of counterfeits, speed the process up, and overcome resistance to careful inspection. Simple means, such as illuminated panels at store registers to help view embedded substrate features, mounted 10-power magnifying glasses to view microfeatures, or a combination of the two to confirm front-to-back registration, are illustrative.
There appears to be a general reticence in the general public and point-of-sale personnel to hold currency up to the light for very careful scrutiny or to examine it under magnification. Therefore, deterrents easily discernible by casual, nearly effortless inspection would be more effective. However, the use of simple, fast authentication devices at point-of-sale locations would also be effective. The committee believes that if such devices were available, the public would accept them just as credit-card authentication is widely accepted.
Simple systems can also be envisioned to render visible simple hidden features, such as ultraviolet fluorescent inks, infrared absorbing inks, and embedded special fibers. More-sophisticated measurement systems can be devised that are more effective, using both overt and covert features, but these will have to be judged on the basis of the cost and reliability requirements. Authentication sensors at each point of sale should cost less than the systems used today to validate credit-card transactions but might be slower, since usually more than one banknote is offered for payment.
Authentication of credit cards has become commonplace and the delays more or less tolerated, because there is a general awareness that they may be stolen or otherwise used fraudulently. Because of this, delays are inevitable, and many merchants employ cash-only registers to help speed the check-out process. Authentication of banknotes should not seriously ompromise the flow of business, hence it is essential that personnel be well- trained, features be designed for ready authentication, and adequate support be commercially available.
Somewhat higher-cost sensor systems are suitable for use in vending and change machines for automatic validation. Many of the proposed innovative visual features can be detected with relatively simple optical systems, such as a light source, filters, and photodetectors. Development of a strategy for machine readability may provide the infrastructure and cost leverage for introducing greater levels of sophistication in point-of-sale devices.
Suggested Citation:"5 Counterfeit-Deterrent Strategies." National Research Council. 1993. Counterfeit Deterrent Features for the Next-Generation Currency Design. Washington, DC: The National Academies Press. doi: 10.17226/2267.
×
PUBLIC EDUCATION AND ACCEPTANCE
By definition, an overt feature is one that can be seen in ambient light by a person with normal vision, with the unaided eye, or with a simple aid. But such a feature cannot be effective if the public is unaware of its existence. Since there is a wide variation in the vision capabilities within the human population, a concentrated effort should be made to define the appropriate metrics for what features can be seen in "ambient light" by a person with "normal vision."
The front line of defense comprises the point-of-sale and transaction personnel who handle currency as a part of their job. Thus, in order to be an effective counterfeit deterrent, visible features must be accepted and widely used by them. Acceptance embodies an understanding of the need (the magnitude of the threat), a confidence that the U.S. government has provided safeguards for the detection of counterfeits, and a visually pleasing appearance for the new banknote designs. Use implies that personnel know what to look for and that feature visibility is sufficient to allow ease of authentication and create minimum delays at the point of sale.
These requirements must be accomplished with a properly designed program of public information and education with emphasis on point-of-sale/transaction personnel. Care must be taken so as not to create a panic; the monetary system has not been flooded with counterfeit banknotes, and older banknote issues are not being recalled. At the same time, however, the public must be made aware that technological advances in copying, scanning, and printing have reached the point where there is indeed a threat that counterfeiting can become widespread.
LAW ENFORCEMENT CONSIDERATIONS
New law enforcement strategies to prevent counterfeiting at the source can be envisioned that respond to the diffuse threat posed by many casual counterfeiters who use readily available reprographic equipment to print a few counterfeit notes each. For example, the ability of law enforcement agents to track copied banknotes back to a specific copier would greatly assist forensic investigations of counterfeiting. Currently, there is no effective reward structure to provide incentives for the public's interception of a counterfeit note close to the initial distribution point. In fact, there is a disincentive to do so, since the finder of a counterfeit note must turn it in without receiving any offsetting compensation. On the other hand, if the compensation were set at too high a level, counterfeiting might then be viewed by the public as a victimless crime in which the government would sustain the loss. This would not assist law enforcement either; if the government made up the entire loss, there would be little incentive for the public to try to identify passers of bogus notes. This is an issue of major public policy. The public is apt to view casual counterfeiting as a small-time fraud that is not seriously harmful.
Suggested Citation:"5 Counterfeit-Deterrent Strategies." National Research Council. 1993. Counterfeit Deterrent Features for the Next-Generation Currency Design. Washington, DC: The National Academies Press. doi: 10.17226/2267.
×
INFORMATION EXCHANGE
Virtually every country in the world now incorporates counterfeiting deterrents in its currency. Thus, there is a wealth of information being generated worldwide about the effectiveness of new features, feature durability, public acceptance, counterfeiting methods, and new features under development. A concerted effort should be mounted to open a pathway by which this information, in as quantitative a form as possible, can be shared to mutual advantage.
For example, the Japanese government has deterrent features built into its currency. Nonetheless, 280 lithographic printed counterfeit 10,000 yen notes (~ $89 each) were recently discovered in the Osaka region. The resulting counterfeiting "scare" led to the shut-down of thousands of ticketing and money-changing machines in the area. Japan's central bank is preparing to issue a new "copy-proof" currency (Brown, 1993b). The effectiveness of these changes in deterring counterfeiting would be of great interest to the Department of Treasury.
There is at present no focused effort to comprehensively record and assess all the incidents and means of counterfeiting U.S. banknotes in all countries of the world. An appropriate data collection system should be instituted so that the entire scope of the counterfeiting threat could be determined.
Suggested Citation:"5 Counterfeit-Deterrent Strategies." National Research Council. 1993. Counterfeit Deterrent Features for the Next-Generation Currency Design. Washington, DC: The National Academies Press. doi: 10.17226/2267.
×
REFERENCES
Brown, J.1993a. Discussion with Special Agent James Brown, U.S. Secret Service, at meeting of the Committee on Next-Generation Currency Design.
Brown, J.1993b. Personal communication from Special Agent James Brown, U.S. Secret Service. August 1993.
Church, S.1993. Personal communication from Sara Church, Bureau of Engraving and Printing. August 1993.
Sellers, J.1993. Personal communication from Jennifer Sellers, Bureau of Engraving and Printing. September 1993.
Suggested Citation:"5 Counterfeit-Deterrent Strategies." National Research Council. 1993. Counterfeit Deterrent Features for the Next-Generation Currency Design. Washington, DC: The National Academies Press. doi: 10.17226/2267.
×
This page in the original is blank.
What Department Combats Counterfieting by Designeing New Ways
Source: https://www.nap.edu/read/2267/chapter/7
Belum ada Komentar untuk "What Department Combats Counterfieting by Designeing New Ways"
Posting Komentar